4.4. Login¶
Loggin to to Supercomputer Fugaku by using local account, logging to login node with using SSH Version2 (Publick key authentication).
Create an SSH key pair (public key and private key) on the user terminal in advance and register the public key from the Fugaku website screen. Register only the public key. When a private key is registered, processing such as temporary suspension of login may be performed as a security measure.
Note
If you change the permissions of the following directories and files under the home directory of the login node, you will not be able to login using ssh.
home directory permission (700)
~/.ssh directory permission (700)
~/.ssh/authorized_keys permission (600)
Do not change these permissions.
4.4.1. Private key/Public key creation¶
To use Supercomputer Fugaku, create the pair of private key and public key on the user device. Recommended creating type is from following.
Ed25519
ECDSA (NIST P 521)
RSA (Key long more than 2048bit) : For how to use RSA keys, refer to “Operation change regarding ssh access to login nodes” on the Fugaku website.
This section describes the procedure for creating key pair of Ed25519 (public / private keys) using UNIX / Linux (OpenSSH) and Windows (puttygen). To use puttygen, it is necessary to install the terminal emulator PuTTY (patty) in advance.
4.4.1.1. Unix/Linux/Mac (OpenSSH)¶
Execute a command ssh-keygen on the user’s device, create a private / public key pair.
Start terminal and execute a command ssh-keygen.
If Mac(OS X), start Terminal() and execute a command ssh-keygen.
If UNIX/Linux, start terminal emulator and execute a command ssh-keygen.
[terminal]$ ssh-keygen -t ed25519 Generating public/private ed25519 key pair. Enter file in which to save the key (/home/username/.ssh/id_ed25519): Enter passphrase (empty for no passphrase): # Enter passphrase Enter same passphrase again: # Re-enter the same passphrase Your identification has been saved in /home/username/.ssh/id_ed25519. Your public key has been saved in /home/username/.ssh/id_ed25519.pub. The key fingerprint is: SHA256:khbWyIyUqMnyjK1Ok78l8EivKbQLNgP3vyhjYBgvif8 namehostname The key's randomart image is: +--[ED25519 256]--+ | ... | | ...+ o | |.o . * . | |=. . o | |=@ + S | |@o% . . | |=%.= . | |*=O = | |+=+=Eo. | +----[SHA256]-----+Note
Set a passphrase that is difficult for others to guess, just like a password. Please be sure to set a passphrase. We recommend a passphrase length of at least 15 characters.
- Once execute ssh-keygen, two types are created: a private key (id_ed25519) and a public key (id_ed25519.pub) on
.sshdirectory under the home directory.Register the public key (id_ed25519.pub) using the Fugaku website.
4.4.1.2. Windows (PuTTYgen)¶
Create a private / public key that can be used with PuTTY / WinSCP with puttygen.
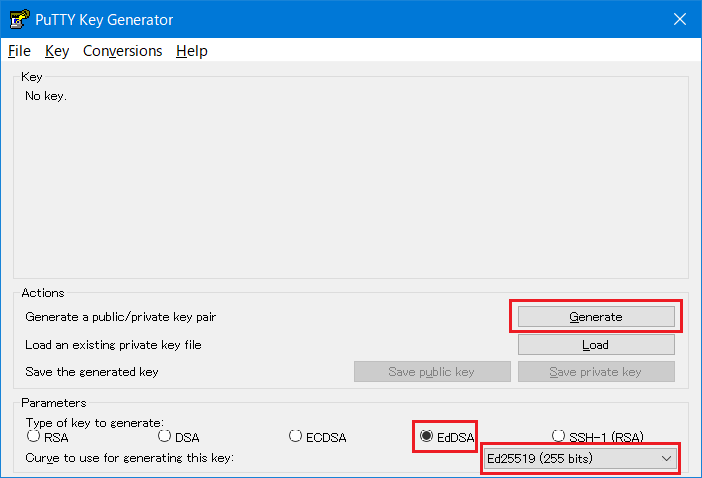
- Start puttygen.Select “EdDSA” for type of key and select “Ed25519 (255 bits)” to generate, then click “Generate”.
Move the mouse cursor randomly.
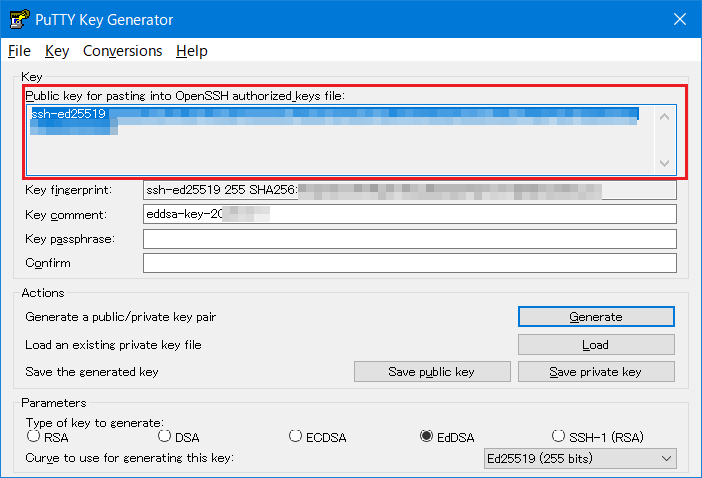
- Save the public key.Copy the displayed contents on “Public key for pasting in to OpenSSH authorized_keys file:” to the clip board (It is recommended to paste on the notepad).The contents pasted on the clip board (Public key) is registered with using the Fugaku website.
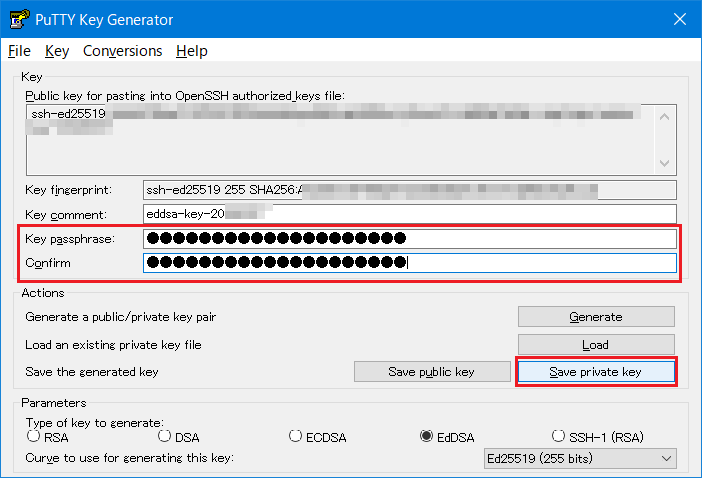
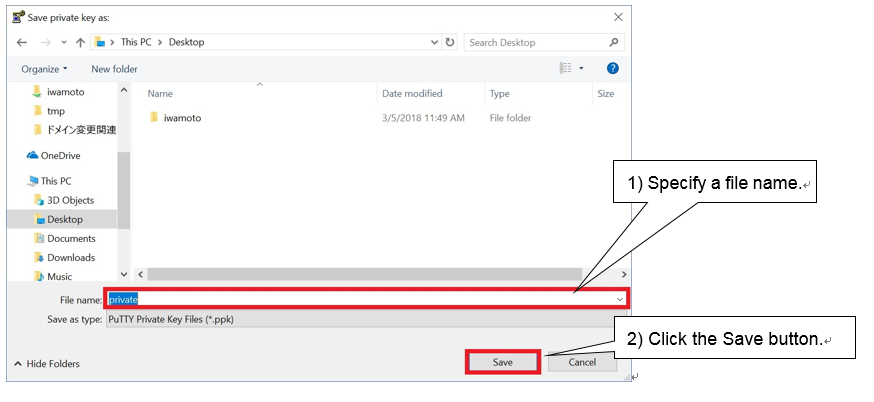
Input a passphrase to both “Key passphrase” and “Confirm passphrase”. After inputting, click “Save private key” and save the private key. Remember to enter your passphrase when you log in to the login node.
Input a file name for storing the private key to “File name(N)”, click “Save(S)”. The private key is stored.
4.4.2. Public key registration¶
4.4.2.1. Registration using Fugaku website¶
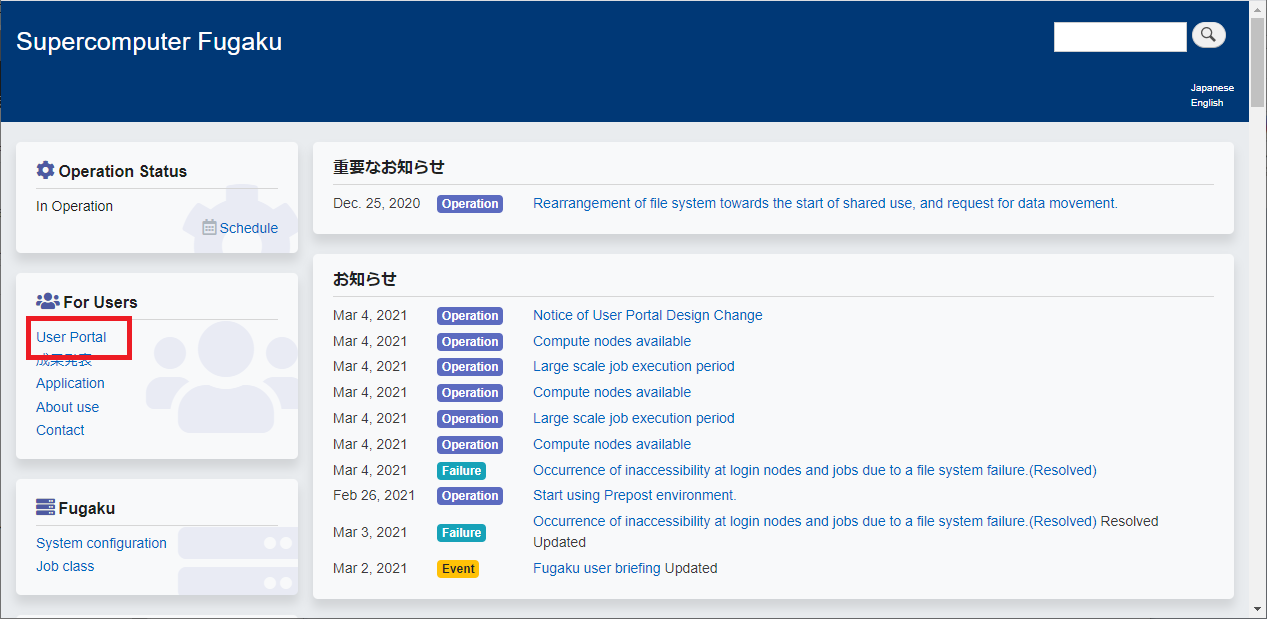
Log in to the Fugaku website(https://www.fugaku.r-ccs.riken.jp/en), then click [User Portal] from menu.
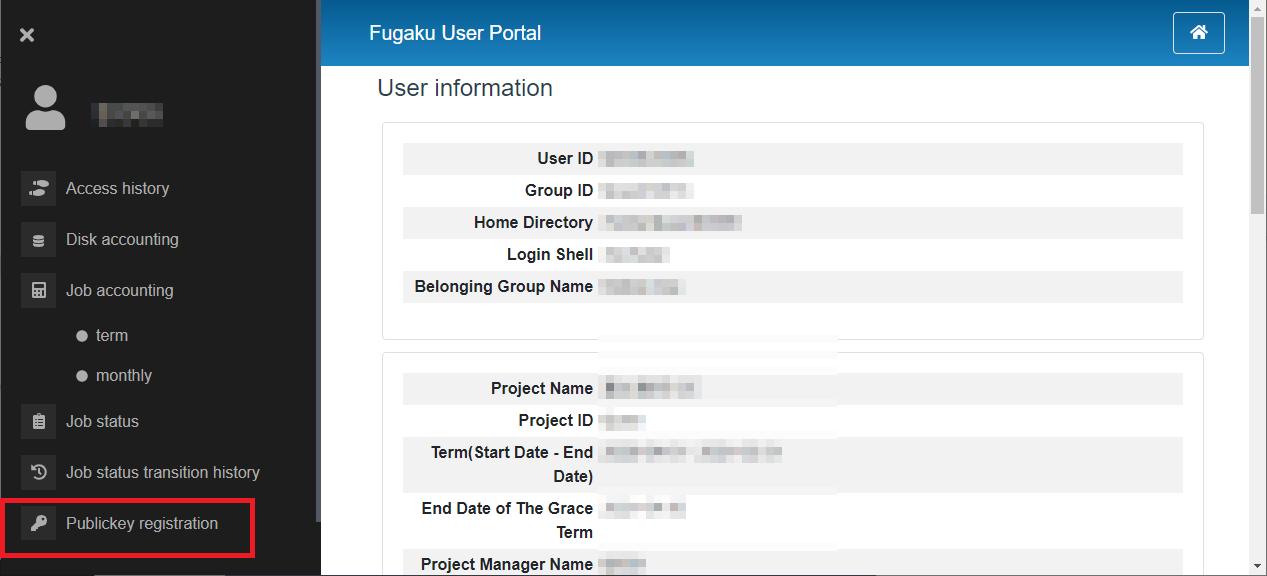
Click [Publickey registration] from menu.
Copy and paste the public key to be used to “Publickey registration” area.
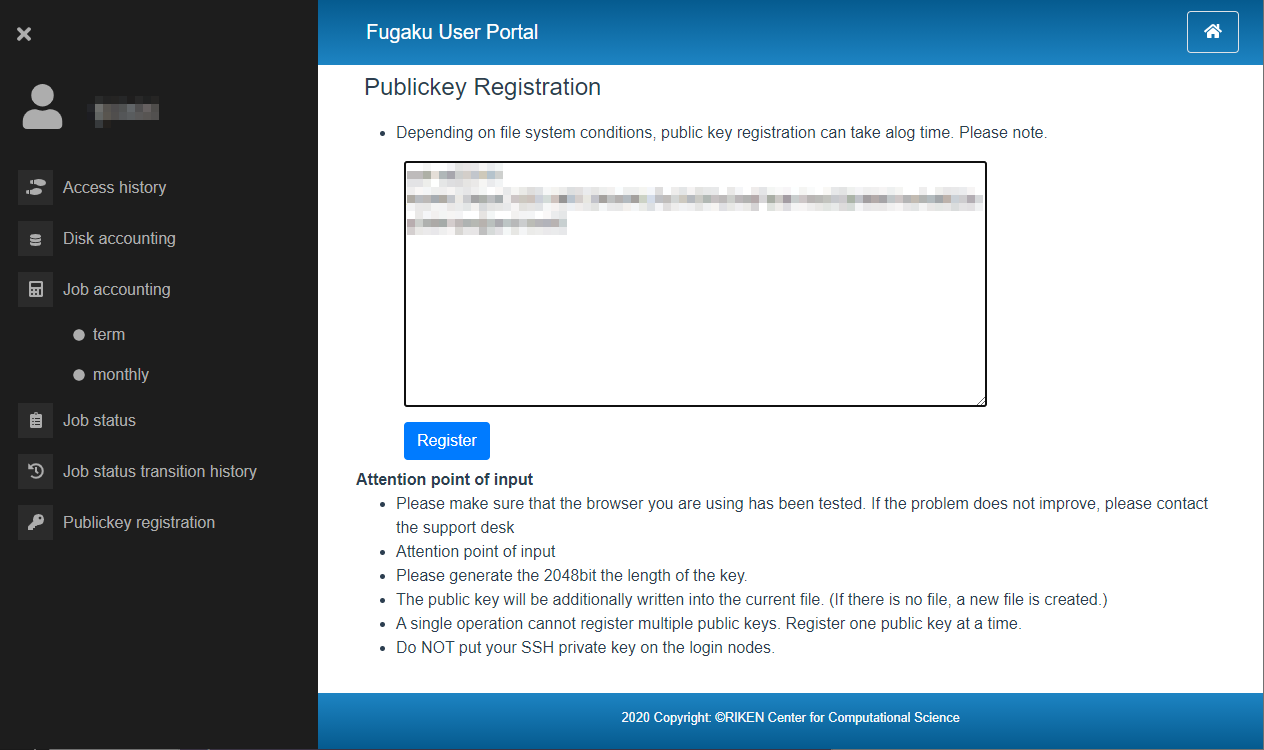
Click [Registar]then register.
Confirm the content and click on [Register].
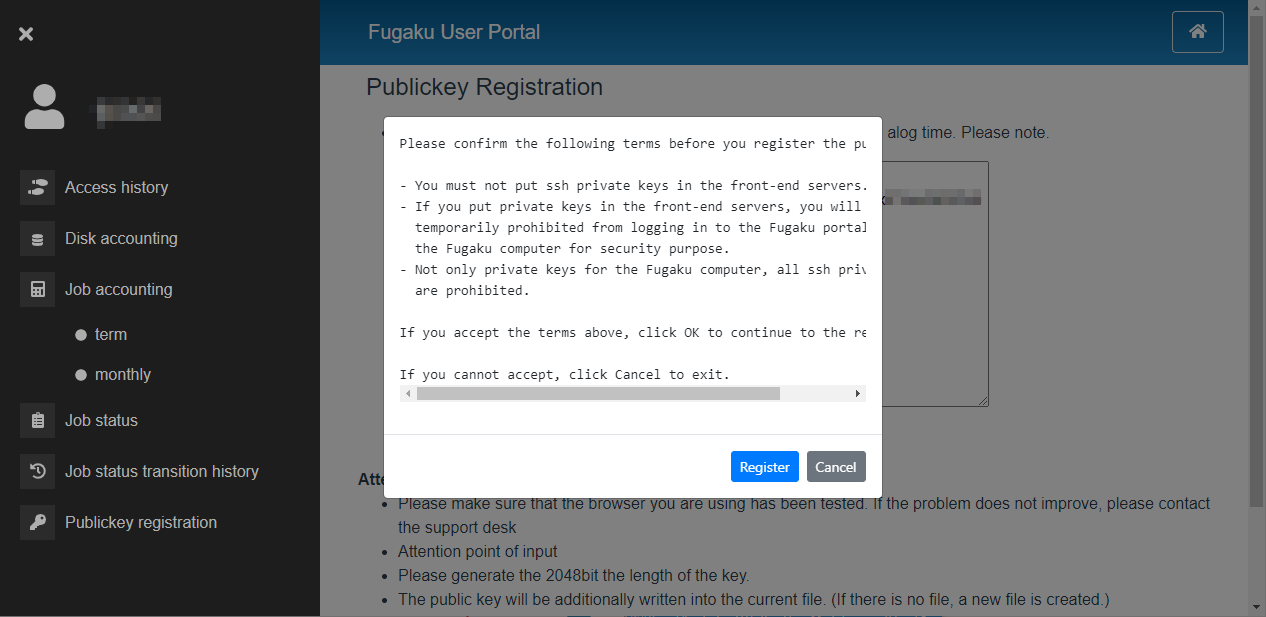
When the “Registration has been Completed.” screen appears, the public key registration is complete.
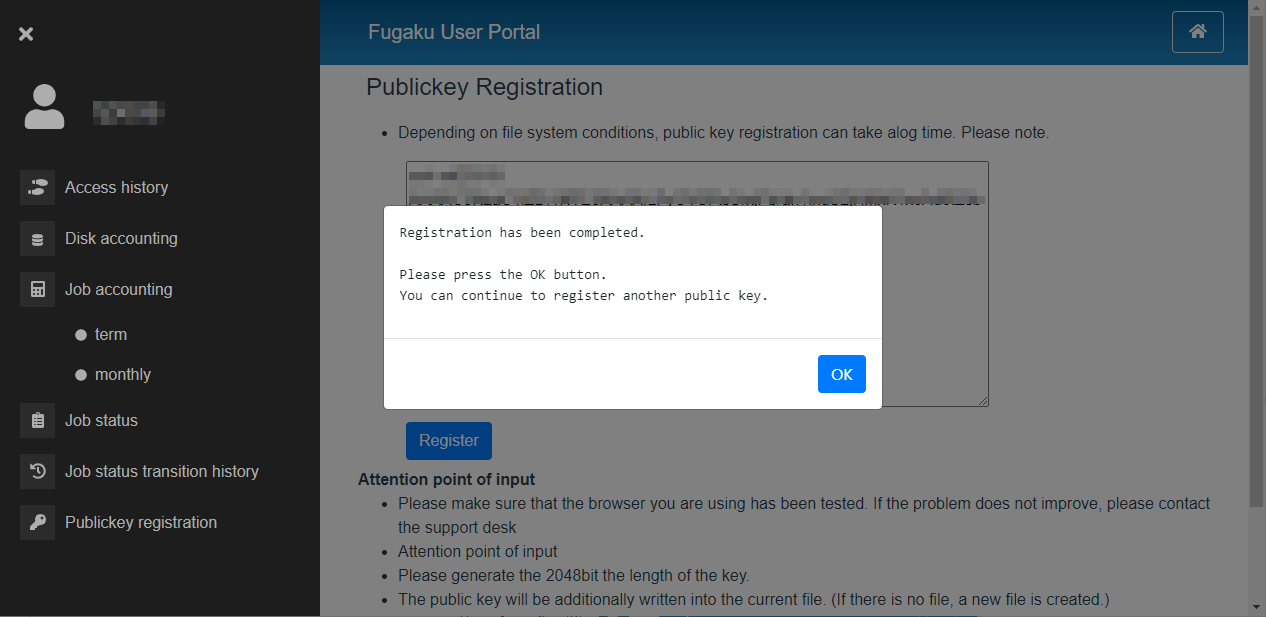
Note
Only one public key can be registered per operation. For the second and subsequent operations, additional registration is required. If you want to register two or more public keys, repeat the same operation.
If the public key is incorrect, an error message will be displayed. Check the public key and execute the registration process again.
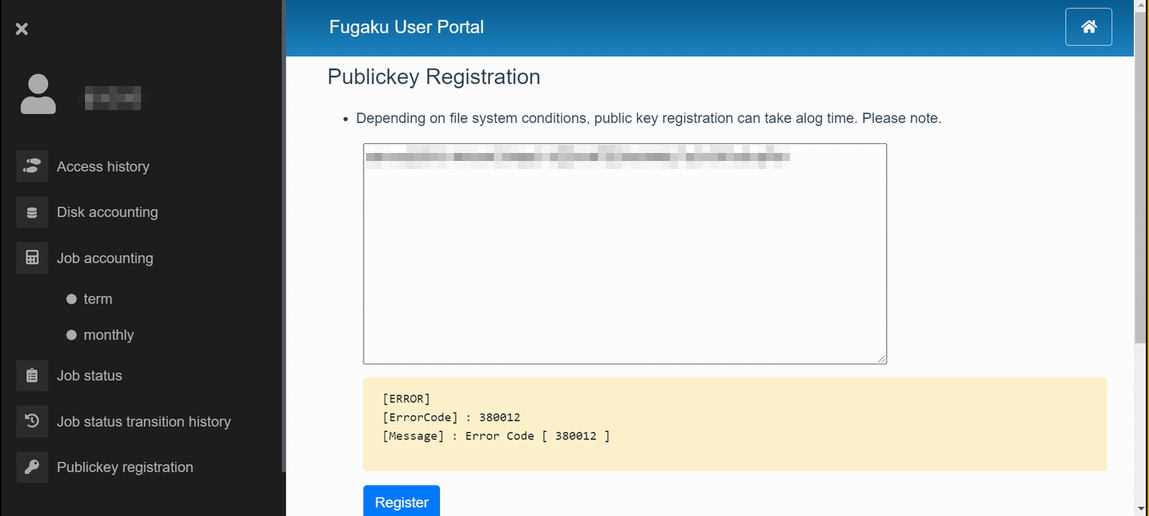
4.4.2.2. Additional registration of public key¶
Edit
~/.ssh/authorized_keyson login node.
[_LNlogin]$ vi ~/.ssh/authorized_keys Press [i] key to enter vi editor insert mode. Click the right mouse button and paste the contents of .ssh / id_rsa.pub. Press the [esc] key, enter [wq!], and press the [Enter] key.
Change permission of private key registered
authorized_keys.
[_LNlogin]$ chmod 600 ~/.ssh/authorized_keys
4.4.3. Accessing direction¶
4.4.3.1. Login node¶
Access by the following host name from the user device
Host name : login.fugaku.r-ccs.riken.jp
This indicates the execution example of ssh command.
[Public key authentication]
[terminal]$ ssh username@login.fugaku.r-ccs.riken.jp
The authenticity of host 'XXXXXX (nnn.nnn.nnn.nnn)' can't be established.
XXXXX key fingerprint is XX: XX: XX: XX: XX: XX: XX: XX: XX:XX:XX:XX:XX:XX:XX:XX.
Are you sure you want to continue connecting (yes/no)? yes # Enter yes (Initial)
Enter passphrase for key '/home/groupname/username/.ssh/id_ed25519': # Enter pass phrase
[_LNlogin]$
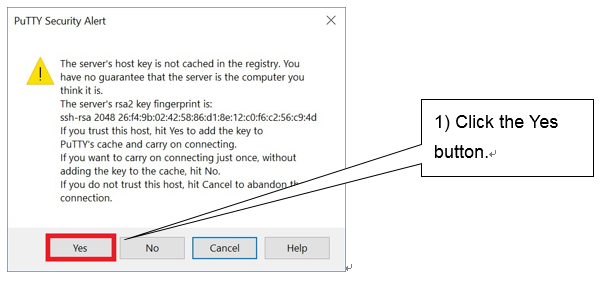
When the first loggin in, the confirmation message about registering the host key (Are you sure you want to continue connecting) is displayed. Enter “yes”.
Specify ssh’s option
-Xto enable X11 Forwarding function when connecting to the login node.Specify ssh’s
-Ato enable SSH Agent-forwarding function when connecting to the login node.Operating the multiple device’s login node. About home area (
/home) and deta area (/vol0n0m/data), share with the each login node. It is the same with the language software environmet.
Note
If you created the key pair by entering the file name of the key file, specify the file name of the key file in the -i option of the ssh command.
[terminal]$ ssh -i key_filename username@login.fugaku.r-ccs.riken.jp
4.4.3.2. Login node (PuTTY)¶
This indicates how to login to the login node with using Windows (PuTTY).
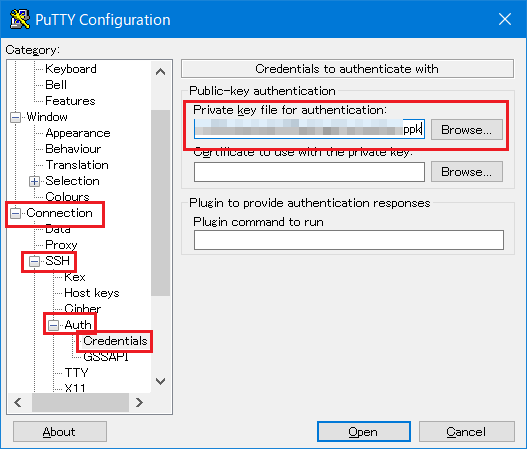
- Start PuTTY. Set the private key which stored in the user device.Click on [Browse] from .Select the pribate key created with puttygen.
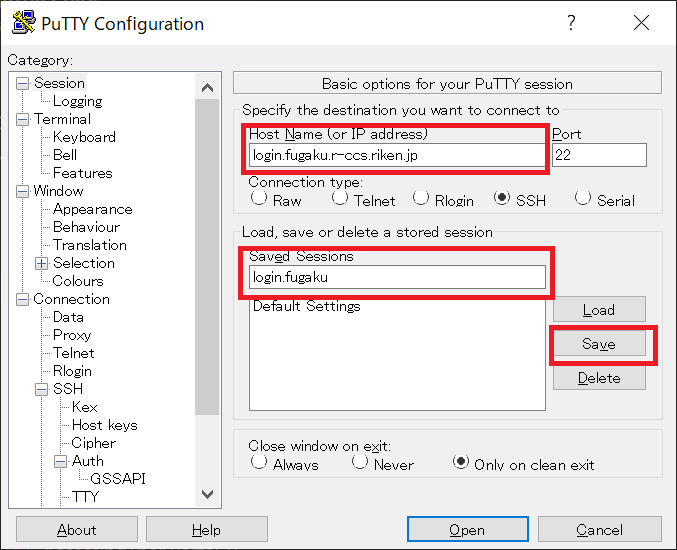
- Select [Session].To [Host Name(or IP address)], enter login node host name
login.fugaku.r-ccs.riken.jp. To save the set contents, input the name to save to [Saved Sessions] and click on [Save]. From the second logging in, select the saved name and click [Load].
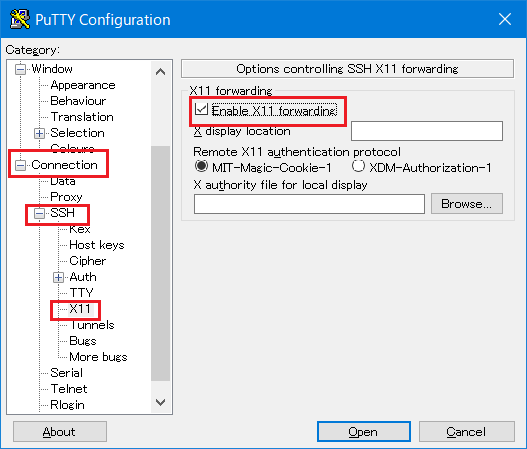
To enable X11 forwarding function when connecting to the login node, before click [Open], open and put the check to [Enable X11 forwarding].
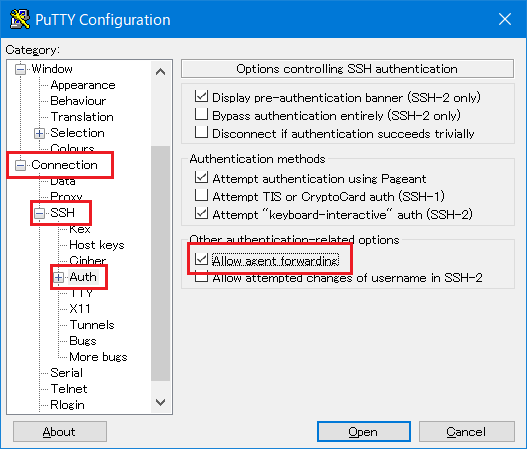
To enable Agent-forwarding function when connecting to the login node, before click [Open], open and put the check to [Allow agent forwarding].
Click on [Open]. It starts connecting to the login node.
When the first login, about the host key registration, the confirmation screen will be shown. Click on “Yes(Y)”.
Input local account name and pass phrase and loging to the login node.
login as: username # Enter a local account Authenticating with public key "imported-openssh-key" Passphrase for key "imported-openssh-key": passphrase # Enter a pass phrase Last login: Tue Mar 27 09:57:12 2018 from xxx.xxx.xxx.xxx login$
4.4.3.3. How to directly specify a login node¶
login.fugaku.r-ccs.riken.jp to access a login node.To specify the login node directly, use the following hostname:.
login1 : login1.fugaku.r-ccs.riken.jp
login2 : login2.fugaku.r-ccs.riken.jp
login3 : login3.fugaku.r-ccs.riken.jp
login4 : login4.fugaku.r-ccs.riken.jp
login5 : login5.fugaku.r-ccs.riken.jp
login6 : login6.fugaku.r-ccs.riken.jp
4.4.3.4. Arm login node¶
The Arm login node is a login node with an Armv8-based Arm processor.
The Arm login node is logged in via the normal login node with Intel CPU. Users cannot log in directly to the Arm login node from the Internet.
Please execute ssh arm1 on the login node to log in.
The host-based authentication is used for the connection between the login node and the Arm login node, so authentication by users is not required .
[_LNIlogin]$ ssh arm1
Last login: XXX MMM DD HH:MM:SS 2020 from 10.4.254.NN
[_LNAlogin]$
The Arm login node is configured as follows:
home area and data area are common to other login nodes. However, NFS mount is used.
Commands such as pjsub and pjstat are not available.
Provides direct Internet access. Proxy setting is not required.
The Arm compiler and LLVM10.0.0 (build with asis) is installed.
When using the compiler, check the module file by executing
module availand set the environment settings properly.
4.4.4. File transfer method¶
login.fugaku.r-ccs.riken.jp for transfer.4.4.4.1. File transfer (sftp)¶
sftp command execution example
[terminal]$ sftp username@k-10g.r-ccs.riken.jp Enter passphrase for key '/home/groupname/username/.ssh/id_rsa': # input passphrase sftp>
File transfer example (put)
sftp> put a.f90 Uploading a.f90 to /home/groupname/username/a.f90 sample.f90 100% 18 0.0KB/s 00:00 sftp>
File transfer example (get)
sftp> get sample.sh.o9110 Fetching sample.sh.o9110 to /home/groupname/username/sample.sh.o9110 sample.sh.o9110 100% 18 0.0KB/s 00:00 sftp>
4.4.4.2. File transfer (scp)¶
scp example of command execution is shown below. (From terminal to login node)
[terminal]$ scp local_file username@k-10g.r-ccs.riken.jp:remote_file Enter passphrase for key '/home/groupname/username/.ssh/id_rsa': # Input passphrase [terminal]$
scp example of command execution is shown below. (Login node to terminal)
[terminal]$ scp username@k-10g.r-ccs.riken.jp:remote_file local_file Enter passphrase for key '/home/groupname/username/.ssh/id_rsa': # Input passphrase [terminal]$
4.4.4.3. Windows (WinSCP)¶
For Windows, use a file transfer program such as WinSCP to transfer the file to the login node. An example of connection with WinSCP is shown below.
Start WinSCP and select [New Site].
Input login node host name (
login.fugaku.r-ccs.riken.jp) to “Host name”.Input the user name to “User name”.
Click on [Advanced…].
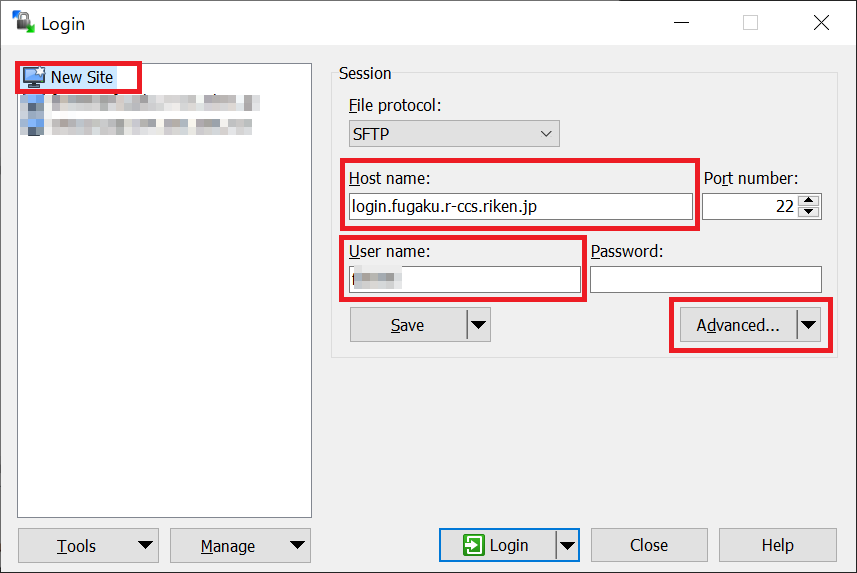
Set the putty private key file name to [Authentication]‘s “Private key file” and click on [OK].
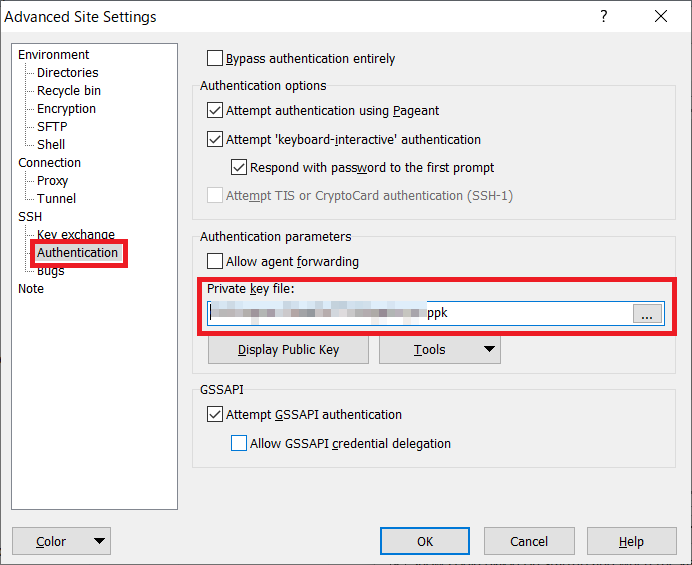
Click on “Save” and save the setting value.
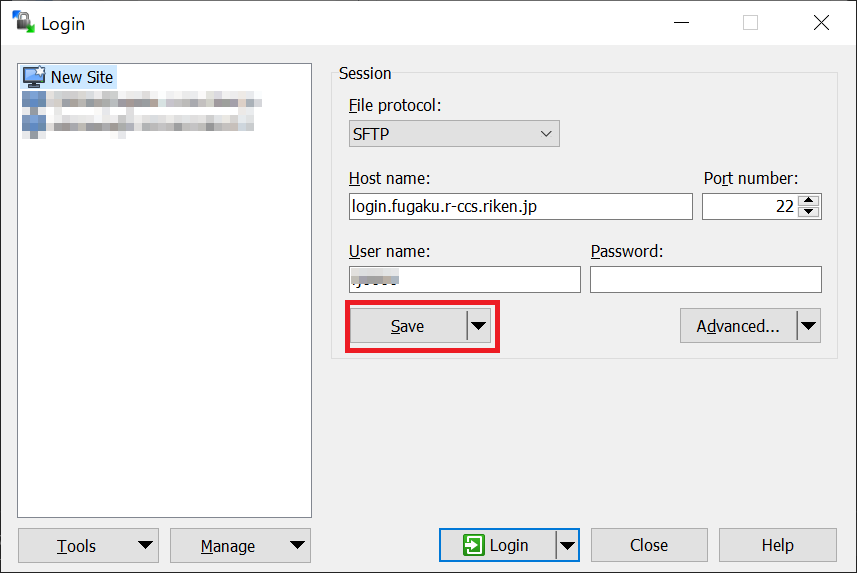
Select the saved setting value and connect by clicking “Login”.
After the connection is completed, a screen similar to Explorer will be displayed, and you can transfer files by dragging and dropping them.
4.4.5. Login shell¶
Login shell is /bin/bash .
4.4.6. E-mail distribution of Fugaku operation information¶
We will send you an email about the following operation information. The content of distribution will be gradually expanded.
Information of jobs affected by a system failure.
Operation information
Others
[How to register your e-mail address]
Create a “.forward” file in the user’s home directory and register the email address that you want to receive.
Examples of “.forward” and filtering configurations will be in the FAQ.
[_LNlogin]$ vi ~/.forward
*****@*****.com